Introduction
When deploying Interspire Email Marketer where the database server is hosted remotely, it is important to secure the connection between the application and the MySQL server.
Interspire as of version 8.5.2 supports SSL/TLS-encrypted database connections, and in this guide you will learn how to secure MySQL connections in Interspire. It will cover both new Interspire installations and existing deployments.
Configure TLS on the MySQL Server
Obtain Server Certificate
You can obtain a publicly trusted SSL/TLS certificate from the usual sources such as a certificate authority, domain registrar, your hosting provider, or an open-access provider such as Let’s Encrypt. You can also elect to use a self-signed certificate if it is appropriate.
There are many excellent guides on how to create a self-signed certificate. For convenience, here is a quick step-by-step rundown on creating one. Please refer to the OpenSSL documentation for more details.
# Generate private key for the CA
openssl genrsa -out ca.key 2048
# Create a self-signed CA certificate
openssl req -x509 -new -nodes -key ca.key -sha256 -days 365 -out ca.crt
# Generate private key for the server
openssl genrsa -out server.key 2048
# Create a certificate signing request (CSR) for the server
openssl req -new -key server.key -out server.csr
# Sign the server certificate using the CA
openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 365 -sha256Once you have the certificate files, upload them to your server. A typical location would be in /etc/mysql/ssl:
/etc/mysql/ssl/
├── ca.crt
├── server.crt
└── server.keyEnsure their permissions are as restricted as possible, such as having them only readable by the mysql user.
Update my.cnf
Configure MySQL to use encryption on network connections.
⚠️ Important: TLS only applies to TCP/IP (network) connections. If Interspire is configured to connect via a local socket (e.g., using localhost), TLS will not be used—even if the certificates are specified1.
Locate and edit the appropriate MySQL configuration file. A typical location would be /etc/mysql/my.cnf. On an Ubuntu-based server running MariaDB, the file location would be /etc/mysql/mariadb.conf.d/50-server.cnf.
Add or uncomment the TLS file location settings as appropriate:
[mysqld]
ssl-ca = /etc/mysql/ssl/ca.crt
ssl-cert = /etc/mysql/ssl/server.crt
ssl-key = /etc/mysql/ssl/server.key
require_secure_transport = ONRestart MySQL to apply the changes:
sudo systemctl restart mysqlNotes
1. MariaDB
Please read the documentation carefully as there are variations between MySQL2, MariaDB3, and the various versions. E.g., MariaDB pre-11.4 and 11.4 and above:
- MariaDB does not support
require_secure_transport. - TLS is enabled if certificates are present, but not enforced without the
GRANT.
2. MySQL on AWS RDS4
- Cannot use self-signed certificates or edit
my.cnf. - TLS is enabled by default.
- Download Amazon’s CA bundle:
- Use
REQUIRE SSLinGRANTto enforce. - Only TCP is supported; no socket or
localhost, which would not make sense in an RDS context.
Verify TLS Support is Active
mysql -u interspire_user -p --ssl-ca=ca.crt --ssl-cert=client.crt --ssl-key=client.key -h your.mysql.hostThen run \s inside the MySQL shell:
...
SSL: Cipher in use is ...
...Enforce SSL per User
Depending on whether you have an existing Interspire instance or not, you may need to coordinate, since if you force SSL on the Interspire database user and Interspire is not yet configured to use TLS, then the database connections will fail.
Depending on how your database user is configured, force SSL with a GRANT:
GRANT ALL PRIVILEGES ON interspiredb.* TO 'interspire_user'@'%' REQUIRE SSL;
FLUSH PRIVILEGES;
Connecting to the database over TCP without TLS/SSL should fail from now on for that user.
Configuring TLS in Interspire
Obtain Client Certificate
Similar to the MySQL server, you need to obtain a certificate for Interspire. The same options to source a certificate are available.
For this guide, we will again use a self-signed certificate for the client (Interspire). You can reuse the server CA file depending on the situation, in this case we did:
openssl genrsa -out client.key 2048
openssl req -new -key client.key -out client.csr
openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out client.crt -days 365 -sha256
Deploy the certificate files. For security reasons, avoid placing the certificate files in the web server document hierarchy. The typical location would be in /etc/mysql/ssl or another explicit path like /opt/interspire/ssl.
Set the permissions to be as restrictive as possible with only the web server user (usually www-data) being able to read them.
Configuring TLS During Installation
If this is a new Interspire installation, you can configure and enable TLS right from the installation wizard:
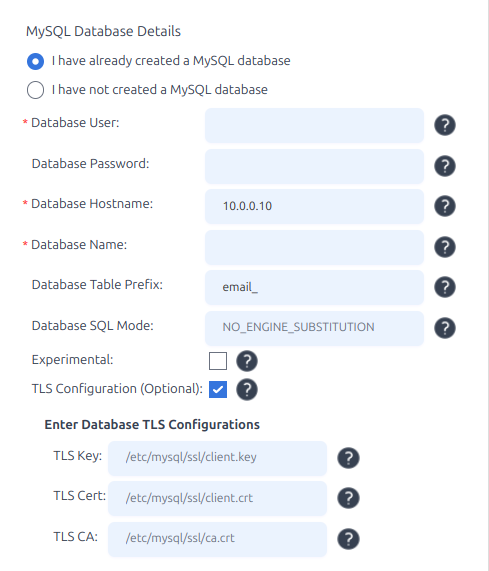
On the MySQL Database Details screen, check “TLS Configuration (Optional)”. Enter the full file paths to:
client.key– your private keyclient.crt– your public client certificateca.crt– certificate authority used to validate the server
Interspire will open an encrypted connection to the database and proceed with the installation.
Configuring TLS Post-Installation
If you already have Interspire installed and running, you can still enable TLS by updating the configuration file:
- Back up and edit the file:
~/admin/includes/config.php - Add or update the following entries:
define('SENDSTUDIO_DATABASE_TLS', '1');
define('SENDSTUDIO_DATABASE_TLS_KEY', '/opt/interspire/ssl/client.key');
define('SENDSTUDIO_DATABASE_TLS_CERT', '/opt/interspire/ssl/client.crt');
define('SENDSTUDIO_DATABASE_TLS_CA', '/etc/mysql/ssl/ca.crt');⚠️ Important: Ensure the SENDSTUDIO_DATABASE_TLS constant is set to '1' to enable TLS.
Verify Interspire is Connecting with TLS
Log in to Interspire. Go to the Tools > System Information page.
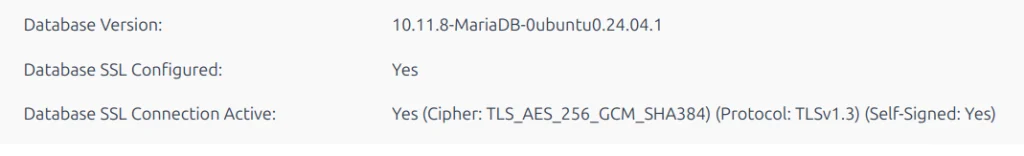
The last two entries on the page will indicate if TLS is enabled and which cipher is being used.
Troubleshooting TLS Connections
TLS Not Active
- Use
127.0.0.1or remote host, notlocalhost SENDSTUDIO_DATABASE_TLSmust be'1'- Confirm user grant with
REQUIRE SSL - Use
\sto check TLS status from the MySQL prompt
Permission Issues
- Ensure files are readable by the web server user
- Use absolute paths, not relative ones
Server Misconfiguration
- Did you restart MySQL?
- Test with MySQL CLI using
--ssl-...options
Wrapping Up
Securing your MySQL connection with TLS is a critical step in protecting sensitive data and aligning with modern security practices. Whether you are deploying Interspire for the first time or retrofitting an existing installation, enabling TLS is straightforward and well-supported.
Footnotes
- For more details, see the MySQL Reference Manual – Connecting to the MySQL Server. On Unix systems, specifying
localhostcauses the MySQL client to connect via a Unix socket, bypassing the TCP/IP stack and any associated TLS configuration. To enforce a secure TLS connection, use127.0.0.1or a resolvable hostname instead. ↩︎ - https://dev.mysql.com/doc/refman/8.4/en/using-encrypted-connections.html ↩︎
- https://mariadb.com/kb/en/securing-connections-for-client-and-server/ ↩︎
- https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.SSL.html ↩︎